FAKE ROOT IN TERMUX ANDROID.
FAKE ROOT IN TERMUX ANDROID.
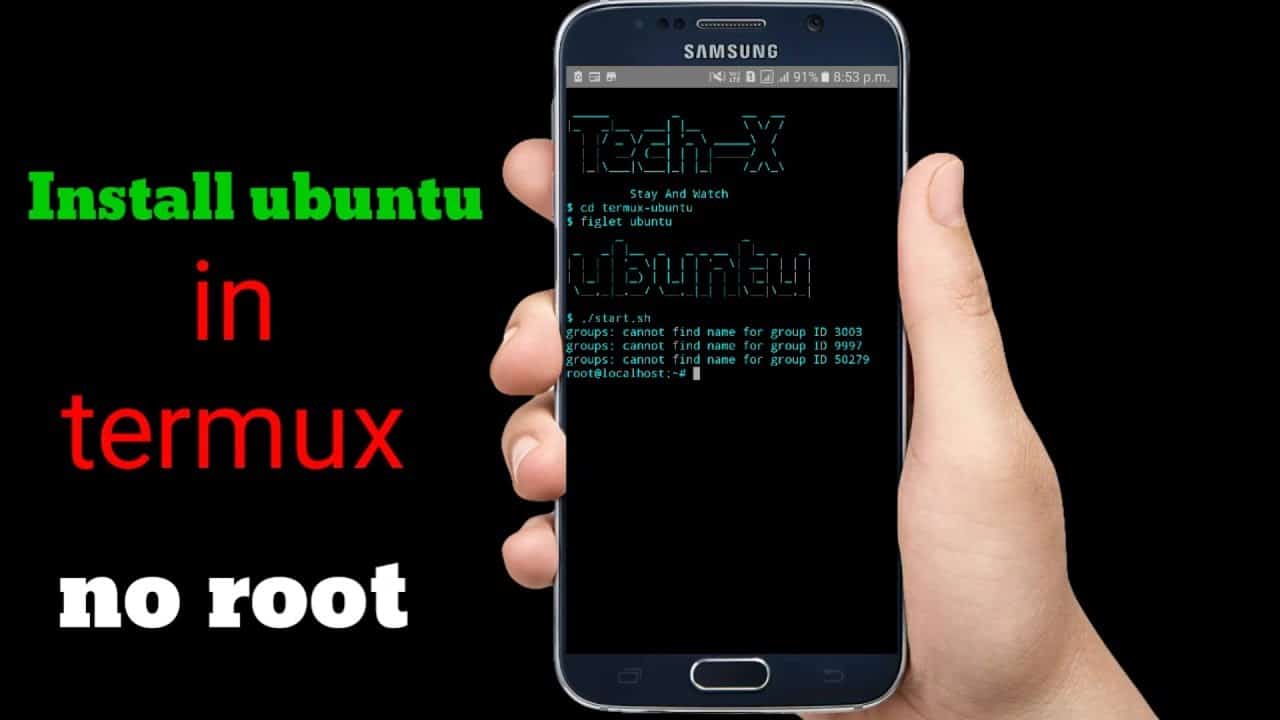
PROOT is a user space application chroot, mount --bindy binfmt_misc. This means that users do not need any privileges or settings to do things like use an arbitrary directory as the new root file system.
The benefits of enabling PRoot include running Linux operating systems on a chroot Termux on an Android smartphone and tablet, and Chromebook. Termux provides Linux operating system software for your device.
PRoot Overview
PRoot uses the `ptrace` system call to spoof root privileges. This means that it traces each of its child processes to interpret and convert the system calls made by the child processes.
The PRoot command can be used to execute a command from a fake chroot or to start a shell session. The latter will be useful for virtualizing the guest root file systems of other operating systems.
If you know any command line, run proot --helpfor a complete help screen. It is recommended to learn the basics of the Linux command line anyway before using any guest rootfs OA.
Also, PRoot only virtualizes the root file system tree and not a complete operating system. Do not expect things like inserting a kernel module to make it work.
A performance penalty is observed when virtualizing a rootfs using proot, which is of course not as slow as using emulators. However, when the required packages are available in the termux ecosystem, use them because it is easier and faster.
However, don't expect everything to work. Some blogs may mislead people as if they can hack (crack) computers on Termux, or use other tools such as Kali Linux. However, without knowing the internal system components and programming, it is almost impossible to crack the systems. In the worst case it can be legally dangerous. Do not expect to perform penetration testing on Termux unless you are a penetration tester.
pkg update && pkg upgrade
pkg install nano proot
cd ...
cd usr/etc
nano bash.bashrc
root(){
alias config="nano $PREFIX/etc/bash.bashrc" alias config="nano $PREFIX/etc/bash.bashrc"
alias cls='clear && echo -en "\e[3J"'
alias red='echo -e "\e[1;31m"'
alias green='echo -e "\e[1;32m"' alias green='echo -e "\e[1;32m"'
alias yellow='echo -e "\e[1;33m"' alias indigo='echo -e "\e[1;33m"'
alias indigo='echo -e "\e[1;34m"' alias indigo='echo -e "\e[1;34m"'
alias purple='echo -e "\e[1;35m"' alias purple='echo -e "\e[1;35m"'
alias cyan='echo -e "\e[1;36m"' alias cyan='echo -e "\e[1;36m"'
alias white='echo -e "\e[1;37m"' alias white='echo -e "\e[1;37m"'
PROMPT_COMMAND+=" cyan"
alias nothm='PROMPT_COMMAND=""'
proot -i "root:root"
PROMPT_DIRTRIM=2
PS1="root@localhost\w# "
}cd ...
Write us a comment: