Ataque MITM: cómo detectarlo y prevenirlo con Bettercap y Wireshark

- 1) ¿Qué compromete un MITM?
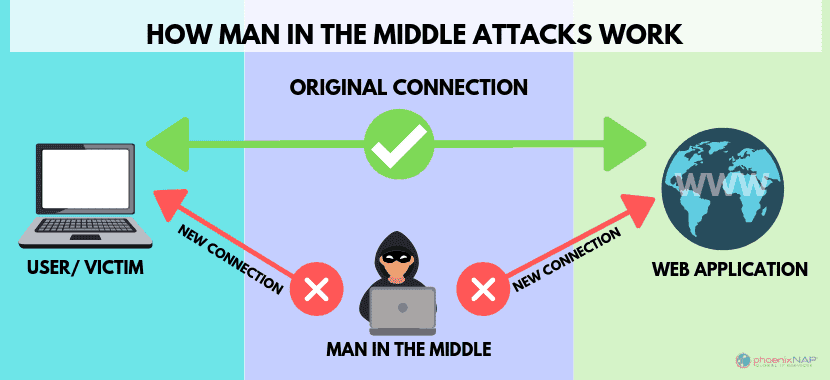
- 2) Cómo funciona un MITM (visión general)
- 3) Laboratorio seguro: entorno de pruebas (no productivo)
- 4) Bettercap: panorama de capacidades (uso responsable)
- 5) Wireshark para detección y análisis
- 6) Medidas de prevención y endurecimiento
- 7) Procedimiento de respuesta ante sospecha de MITM
- 8) Bettercap y Wireshark en laboratorio: qué sí y qué no hacer
- 9) Checklist rápido de endurecimiento
- 10) Preguntas frecuentes
- 11) Glosario mínimo
- 12) Recursos recomendados
- 13) Enlaces internos sugeridos
Un ataque Man-in-the-Middle (MITM) ocurre cuando un tercero se interpone entre dos extremos que se comunican (por ejemplo, un usuario y un sitio web) y escucha, altera o bloquea la información sin que las partes lo perciban. Este artículo explica, con enfoque académico y de concienciación, cómo funciona MITM, cómo realizar pruebas controladas en un laboratorio privado (no productivo) y, sobre todo, cómo detectar y mitigar este tipo de amenazas con Wireshark y buenas prácticas de red. Cumple con políticas de monetización al priorizar la seguridad, la defensa y el uso ético.
Aviso legal y ético: la información de este artículo se ofrece únicamente para formación en ciberseguridad, auditorías autorizadas y laboratorios privados. No se proporcionan pasos operativos para vulnerar sistemas. El uso indebido puede ser ilegal. Actúa siempre con permiso explícito y en entornos de prueba.
1) ¿Qué compromete un MITM?
- Confidentiality: el atacante puede leer datos sensibles (credenciales, cookies, tokens).
- Integridad: puede inyectar o modificar contenido en tránsito (scripts, formularios, redirecciones).
- Disponibilidad: puede degradar el servicio o interrumpir la conversación (p. ej., anulando respuestas o cortando sesiones).
Ejemplo conceptual: dos empleados intercambian un contrato por correo. Un intruso, situado entre ellos, se entera del horario de envío (falla de confidencialidad), intercepta y cambia una cláusula (falla de integridad) y, si decide borrar el adjunto, impide la entrega (falla de disponibilidad).
2) Cómo funciona un MITM (visión general)
- En LAN: suplantación ARP (ARP spoofing) y ataques a protocolos de descubrimiento para redirigir tráfico a la máquina del atacante.
- En Wi-Fi: evil twin (punto de acceso clonado), desautenticación, caída de cifrados débiles (WEP/WPA obsoletos) y Captive Portal phishing.
- En DNS: envenenamiento o secuestro de respuestas para enviar a la víctima a dominios falsos.
- En HTTP/TLS: downgrade o falsos certificados si no hay pinning, HSTS o validaciones robustas.
En esencia, el atacante se posiciona como “router temporal” o “proxy transparente”, reencaminando paquetes para leerlos o alterarlos. Si el canal está cifrado correctamente (TLS moderno + HSTS + validaciones), la ventana de oportunidad se reduce drásticamente.
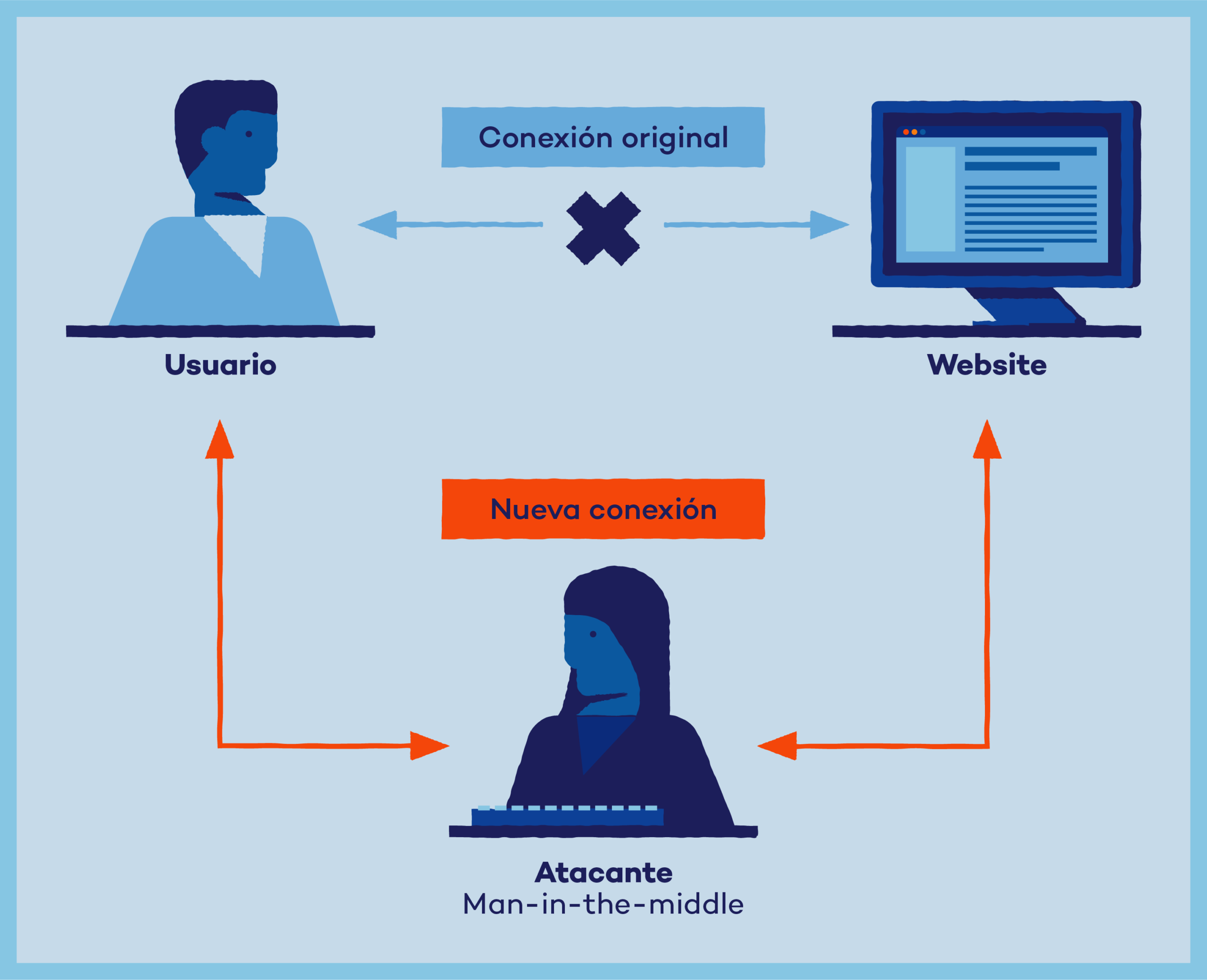
3) Laboratorio seguro: entorno de pruebas (no productivo)
Para comprender la detección (no la explotación), crea un laboratorio aislado con tres equipos o VMs: Cliente, Servidor y Analista. Usa una red virtual o un switch dedicado sin acceso a Internet. En el equipo Analista instala herramientas de observación de tráfico y solo ejecuta acciones con autorización. No usaremos pasos operativos de intrusión; el objetivo es capturar, visualizar y reconocer patrones en un laboratorio.
4) Bettercap: panorama de capacidades (uso responsable)
Bettercap es un framework de red para pruebas de seguridad autorizado. En laboratorios se utiliza para simular escenarios de red (sondeo de hosts, inspección de tráfico, pruebas de suplantación) con fines educativos. No incluimos comandos de explotación; en cambio, resumimos módulos y buenas prácticas:
- Descubrimiento: inventario de hosts, servicios y protocolos activos en un segmento.
- Inspección: lectura de metadatos de tráfico (quién habla con quién, puertos, volúmenes).
- Proxy educativo: demostraciones de por qué es crucial HTTPS, HSTS y la validación de certificados.
- Extensibilidad: scripts y sniffers para usos legítimos en auditorías con permiso.
Buenas prácticas: documenta permisos por escrito, delimita el alcance (red/lab), define horarios, guarda evidencias y valida contramedidas con el responsable de TI. El objetivo es mejorar la seguridad, no vulnerarla.
5) Wireshark para detección y análisis
Wireshark es el analizador de protocolos líder. En detección de MITM nos ayuda a identificar anomalías típicas en ARP, DNS y TLS. A continuación, filtros orientativos (seguros) para investigar signos de MITM en un laboratorio:
- ARP sospechoso: direcciones MAC diferentes que se atribuyen la misma IP en poco tiempo. Filtros útiles:
arp,arp.duplicate-address-detected == 1,arp.opcode == 2. - Patrones de reenvío extraños: múltiples respuestas ARP “gratuitas” desde un host que no es el gateway legítimo. Observa
eth.srcvs. MAC del router. - DNS anómalo: respuestas con TTL inusualmente bajo o servidores DNS “no corporativos”. Filtros:
dns,dns.flags.rcode != 0,ip.addr == <dns_sospechoso>. - Downgrade/Errores TLS: servidores que negocian suites obsoletas o cambios de HTTPS a HTTP. Filtros:
tls,http && tcp.port == 80, y seguimiento de flujo. - Tráfico redirigido: picos de
ICMP redirecto rutas inesperadas (mira la columna “Next Hop”).
Wireshark también permite “seguir flujo TCP/HTTP” para visualizar si hay inserción de contenido o modificación de cabeceras. En un entorno sano, no deberías ver manipulación de Location, Set-Cookie sin banderas seguras o downgrade a HTTP.
6) Medidas de prevención y endurecimiento
- Todo HTTPS, todo el tiempo: aplica HSTS, TLS 1.2/1.3, Perfect Forward Secrecy y deshabilita suites débiles.
- Validación fuerte de certificados: considera certificate pinning en apps críticas y monitorea caducidades.
- WPA3 y segmentación: usa cifrado moderno en Wi-Fi, VLANs por rol y separa invitados de recursos internos.
- Protecciones de switching: DHCP Snooping, Dynamic ARP Inspection, IP Source Guard y port security.
- DNS seguro: DNSSEC en dominios propios y resolutores confiables con DNS-over-HTTPS/TLS cuando aplique.
- VPN corporativa: todo tráfico de usuarios remotos debería ir encapsulado y autenticado.
- Autenticación robusta: 802.1X/NAC para controlar quién entra a la red de capa 2.
- Higiene del navegador: bloquea mixed content, activa
SecureyHttpOnlyen cookies, ySameSiteadecuado. - Concienciación: forma a usuarios para reconocer portales falsos y advertencias de certificado.
7) Procedimiento de respuesta ante sospecha de MITM
- Contención: aísla el segmento o el puerto sospechoso; revoca accesos del host comprometido.
- Adquisición de evidencias: captura pcap en el switch (port mirroring) y en el endpoint afectado.
- Análisis: revisa ARP, DNS, TLS en Wireshark con los filtros anteriores y correlaciona con logs.
- Erradicación: restaura configuraciones de red, limpia equipos, renueva credenciales y claves.
- Lecciones aprendidas: ajusta políticas, segmentación y monitorización para evitar recurrencias.
8) Bettercap y Wireshark en laboratorio: qué sí y qué no make
- Sí: usar Bettercap en un laboratorio privado y autorizado para demostrar la necesidad de HTTPS, HSTS y controles de red, sin publicar ni compartir material sensible.
- Sí: emplear Wireshark para entender protocolos, validar configuraciones y detectar anomalías.
- No: ejecutar suplantación ARP/DNS, proxies o inyecciones en redes ajenas o productivas.
- No: automatizar scripts de intrusión ni compartir capturas con datos reales.
9) Checklist rápido de endurecimiento
- Forzar HTTPS + HSTS en todos los dominios propios.
- Inventariar y desactivar cifrados obsoletos en servidores.
- Aplicar WPA3 y contraseñas únicas por SSID; segmentar redes de invitados.
- Activate DHCP Snooping y ARP Inspection en switches de acceso.
- Usar DNS firmado y resolutores confiables; bloquear DNS externo no autorizado en el perímetro.
- Revisar cookies (Secure, HttpOnly, SameSite) y cabeceras (CSP, XFO, Referrer-Policy).
- Monitorizar con IDS/IPS patrones de suplantación y redirecciones anómalas.
- Formar a usuarios sobre avisos de certificados y portales maliciosos.
10) Preguntas frecuentes
¿Bettercap es legal? Sí, cuando se usa con autorización explícita y en laboratorios o auditorías. No debe emplearse para vulnerar sistemas ajenos.
¿Cómo sé si alguien intenta un MITM en mi red? Revisa tablas ARP del gateway, alertas del IDS y capta tráfico con Wireshark buscando duplicados ARP, DNS no corporativos y fallos TLS.
¿HTTPS me protege totalmente? Reduce drásticamente el riesgo, especialmente con HSTS y validación estricta. Aun así, mantén higiene en endpoints y red.
11) Glosario mínimo
- ARP: protocolo que asocia IPs con direcciones MAC en LAN.
- HSTS: cabecera que obliga al navegador a usar siempre HTTPS con un dominio.
- DNSSEC: extensiones de seguridad para validar respuestas DNS.
- Certificate pinning: técnica que “ancla” certificados esperados en una app.
12) Recursos recomendados
- Documentación oficial de Wireshark
- Sitio oficial de Bettercap
- OWASP Proactive Controls
- NIST publicaciones de seguridad
13) Enlaces internos sugeridos
- Informática Colectiva — Ciberseguridad (guías y novedades)
- Cómo elegir temáticas seguras para monetización (buenas prácticas de contenido)
Conclusion: un MITM exitoso suele aprovechar configuraciones débiles en LAN/Wi-Fi y la falta de cifrado estricto. La combinación de HTTPS bien aplicado, protecciones de capa 2 en switches, segmentación, DNS seguro y la monitorización con Wireshark reduce el riesgo de forma significativa. Utiliza Bettercap únicamente para demostraciones aprobadas y reforzar la cultura de seguridad en tu organización.

Write us a comment: